

















Do you want to contribute by writing guest posts on this blog?
Please contact us and send us a resume of previous articles that you have written.
Is America's Data at Risk? Federal Cybersecurity Under Scrutiny

In today's interconnected world, data has become one of the most valuable assets for individuals, organizations, and nations alike. The United States, being a global leader in technology and innovation, possesses an extensive amount of sensitive data that is at constant risk from cyber threats. From government agencies to critical infrastructure, the nation's cybersecurity measures are paramount to ensure the protection and integrity of data.
The Evolving Threat Landscape
As technology advances and cybercriminals become more sophisticated, the threat landscape has undergone a significant transformation. Hackers, both state-sponsored and individual actors, target critical infrastructure, government systems, and private entities to breach data and wreak havoc. The motive behind these attacks could range from financial gain to gathering sensitive intelligence or disrupting essential services.
The urgency to bolster the nation's cybersecurity measures has never been greater. The rapid adoption of advanced technologies like artificial intelligence, Internet of Things (IoT),and cloud computing has expanded the attack surface, providing more opportunities for cyber threats to exploit vulnerabilities.
4.1 out of 5
| Language | : | English |
| File size | : | 685 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Word Wise | : | Enabled |
| Print length | : | 250 pages |
| Lending | : | Enabled |
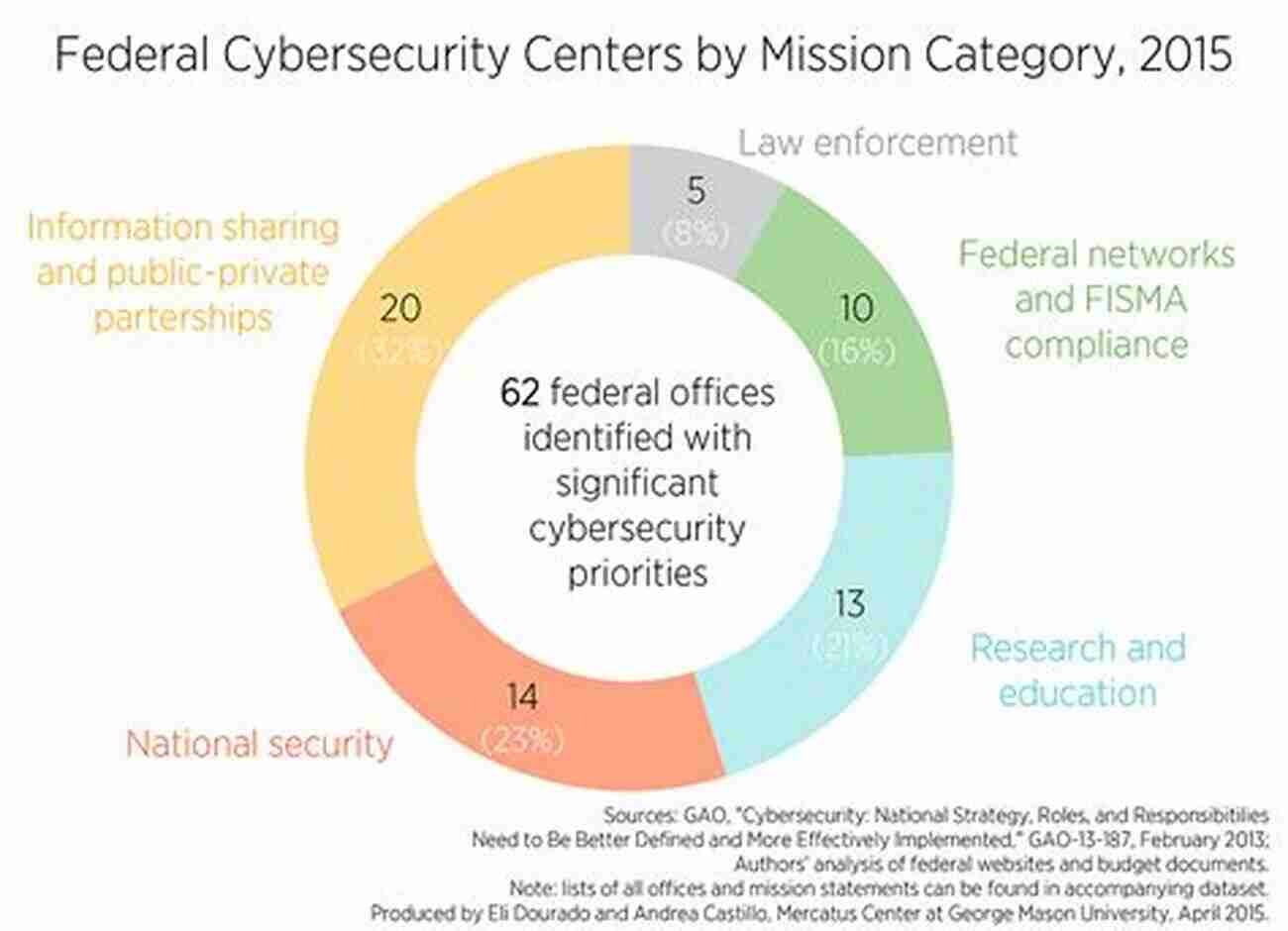
Federal Government's Role in Cybersecurity
The federal government plays a vital role in safeguarding the nation's data and infrastructure from cyber threats. Agencies such as the Department of Homeland Security (DHS),National Security Agency (NSA),and Cybersecurity and Infrastructure Security Agency (CISA) work together to establish and enforce cybersecurity policies, conduct threat intelligence, and respond to incidents.
The Federal Information Security Modernization Act (FISMA) and the Cybersecurity Enhancement Act provide a framework for federal agencies to strengthen their cybersecurity posture. The implementation of these acts ensures that agencies regularly assess risks, develop mitigation strategies, and report any incidents promptly. However, the evolving threat landscape demands continuous collaboration, innovation, and investment to counter emerging cyber threats.
America's Critical Infrastructure in the Crosshairs
The protection of critical infrastructure, such as power grids, transportation systems, and financial institutions, is an essential part of national security. The increasing connectivity of these systems poses a significant challenge as any disruption can have severe consequences on the economy, public safety, and daily life.
Cybersecurity vulnerabilities in critical infrastructure were evident during the 2015 Ukraine power grid attack and the recent ransomware attack on the Colonial Pipeline. These incidents highlight the need for robust security measures to protect against cyber threats that can potentially paralyze critical infrastructure and cause widespread disruption.
Securing the Government's Digital Domain
Government agencies house a vast amount of sensitive data, including classified information, personally identifiable information (PII),and intellectual property. The protection of such data is crucial for preserving national security, upholding privacy rights of citizens, and maintaining trust in government institutions.
While federal agencies have made significant strides in improving their cybersecurity posture, high-profile breaches like the Office of Personnel Management (OPM) hack in 2015 have raised concerns about the effectiveness of existing measures. Continuous efforts to enhance workforce training, modernize legacy systems, establish real-time threat intelligence sharing, and implement robust identity management protocols are essential to tackle these challenges.
The Role of Public-Private Collaboration
Cybersecurity is not solely the responsibility of the federal government; it requires the active participation and collaboration of the private sector as well. Many critical infrastructures and key industries are owned and operated by private entities, making their involvement critical in defending against cyber threats.
The sharing of threat intelligence, best practices, and expertise between the government and private sector can significantly strengthen the nation's cybersecurity posture. Collaborative efforts, such as the Department of Defense's Cybersecurity Maturity Model Certification (CMMC) program, aim to ensure adequate security controls and practices are implemented by contractors working with sensitive government data.
The United States faces an ever-increasing cyber threat landscape that puts the nation's data, critical infrastructure, and overall security at risk. By recognizing the evolving nature of cyber threats and adapting to emerging challenges, the federal government can play a significant role in securing America's digital domain.
Collaboration between public and private entities, continuous investment in cybersecurity measures, and the pursuit of innovative solutions can help mitigate risks and protect the nation's sensitive data. Harnessing the power of technology and human ingenuity, America can overcome the challenges of the digital era and ensure a safer, more secure future for all.
4.1 out of 5
| Language | : | English |
| File size | : | 685 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Word Wise | : | Enabled |
| Print length | : | 250 pages |
| Lending | : | Enabled |
Federal government agencies are the frequent target of cybersecurity attacks. From 2006 to 2015, the number of cyber incidents reported by federal agencies increased by more than 1,300 percent. In 2017 alone, federal agencies reported 35,277 cyber incidents. The Government Accountability Office (“GAO”) has included cybersecurity on its “high risk” list every year since 1997.
No agency is immune to attack and the list of federal agencies compromised by hackers continues to grow. In the past five years, agencies reporting data breaches include the United States Postal Service, the Internal Revenue Service, and even the White House. One of the largest breaches of government information occurred in 2015 when a hacker ex-filtrated over 22 million security clearance files from the Office of Personnel Management (“OPM”). Those files contained extensive personal and potentially comprising information. We may never know the full impact on our national security of the OPM breach.
The number of data breaches agencies have reported in recent years is not surprising given the current cybersecurity posture of the federal government. A recent report by the Office of Management and Budget (“OMB”) made clear that agencies “do not understand and do not have the resources to combat the current threat environment.” This is especially concerning given the information agencies must collect and hold. This report documents the extent to which the federal government is the target of cybersecurity attacks, how key federal agencies have failed to address vulnerabilities in their IT infrastructure, and how these failures have left America’s sensitive personal information unsafe and vulnerable to theft.

 Samuel Ward
Samuel WardTake Control Of Your Network Marketing Career
Are you tired of working...

 Bryson Hayes
Bryson HayesThe Enigmatic Talent of Rype Jen Selk: A Musical Journey...
When it comes to musical prodigies,...

 Norman Butler
Norman ButlerUnveiling the Rich History and Poetry of Shiraz in...
When it comes to the cultural...

 Cade Simmons
Cade SimmonsHow Impatience Can Be Painful In French And English
: In today's fast-paced world, impatience...

 William Shakespeare
William ShakespeareSewing For Sissy Maids - Unleashing Your Creative Side
Are you ready to dive...

 Harry Hayes
Harry HayesGST Compensation to States: Ensuring Fiscal Stability...
In the wake of the COVID-19 pandemic,...

 Rodney Parker
Rodney ParkerLearn How to Play Blackjack: A Comprehensive Guide for...
Blackjack, also known as twenty-one, is one...

 Wade Cox
Wade CoxComplete Guide Through Belgium And Holland Or Kingdoms Of...
Welcome, travel enthusiasts, to a...

 Jack Butler
Jack Butler15 Eye Popping Projects To Create with Felt Decorations
Felt decorations have become a popular craft...

 Dennis Hayes
Dennis HayesFirst Aid For Teenager Soul Mini Book Charming Petites...
The teenage years can...

 Brett Simmons
Brett SimmonsFrom Fear To Freedom - Overcoming Your Fears and Living a...
Are you tired of living in...

 Carl Walker
Carl WalkerSmoking Ears And Screaming Teeth: The Shocking Truth...
Smoking has long been known to cause a host of...
Light bulbAdvertise smarter! Our strategic ad space ensures maximum exposure. Reserve your spot today!

 F. Scott FitzgeraldThe Cistern Mission: Unveiling the Reality of Michael Dadich's Extraordinary...
F. Scott FitzgeraldThe Cistern Mission: Unveiling the Reality of Michael Dadich's Extraordinary...
 Graham BlairGet ready for an Epic Adventure: Captain Awesome Saves The Winter Wonderland!
Graham BlairGet ready for an Epic Adventure: Captain Awesome Saves The Winter Wonderland!
 Percy Bysshe ShelleyDay Section Hikes Pacific Crest Trail Southern California: Exploring the...
Percy Bysshe ShelleyDay Section Hikes Pacific Crest Trail Southern California: Exploring the...
 Shaun NelsonThe Oxford Handbook Of The Incas: A Glimpse Into the Marvels of an Ancient...
Shaun NelsonThe Oxford Handbook Of The Incas: A Glimpse Into the Marvels of an Ancient... Donovan CarterFollow ·2.8k
Donovan CarterFollow ·2.8k David PetersonFollow ·8.2k
David PetersonFollow ·8.2k Gene PowellFollow ·11k
Gene PowellFollow ·11k Orson Scott CardFollow ·15.4k
Orson Scott CardFollow ·15.4k Benji PowellFollow ·4.7k
Benji PowellFollow ·4.7k Colin FosterFollow ·2.3k
Colin FosterFollow ·2.3k Hassan CoxFollow ·7.8k
Hassan CoxFollow ·7.8k Roy BellFollow ·15.5k
Roy BellFollow ·15.5k














