

















Do you want to contribute by writing guest posts on this blog?
Please contact us and send us a resume of previous articles that you have written.
How To Become A Cyber Security Analyst - The Ultimate Guide


In today's interconnected world, cyber threats have become more prevalent than ever before. Malicious hackers constantly seek to exploit vulnerabilities in computer networks and systems, causing significant damage to individuals, organizations, and even nations.
As a result, the demand for skilled professionals who can effectively protect against these cyber threats has skyrocketed. If you have a passion for technology, problem-solving, and a desire to make a real difference, becoming a Cyber Security Analyst might be the career path for you.
What Does a Cyber Security Analyst Do?
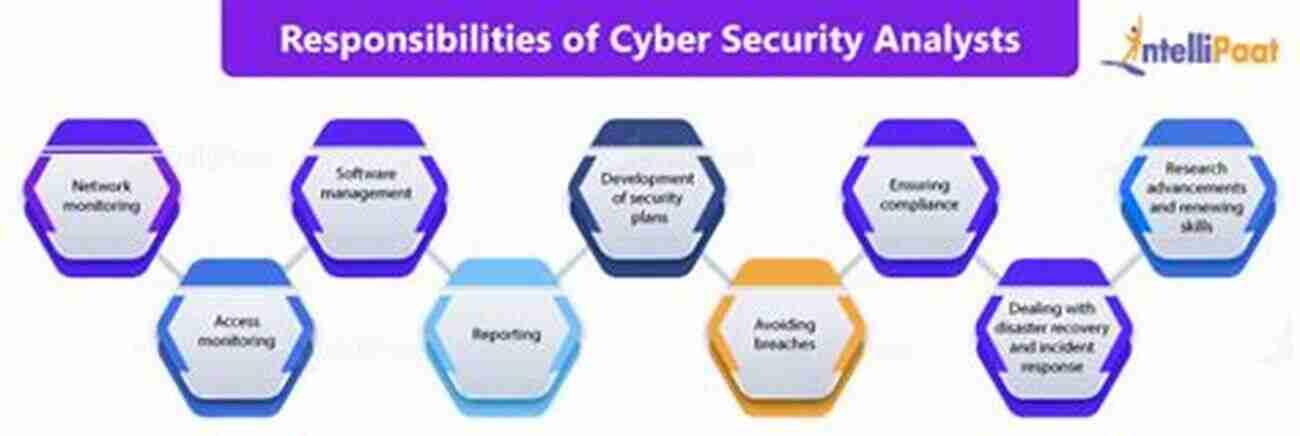
A Cyber Security Analyst is responsible for identifying potential vulnerabilities and protecting computer networks and systems from unauthorized access, attacks, and data breaches. Their role involves:
4.3 out of 5
| Language | : | English |
| File size | : | 16701 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Word Wise | : | Enabled |
| Print length | : | 281 pages |
| Lending | : | Enabled |
- Conducting regular security assessments and audits to identify weaknesses
- Planning and implementing security measures to protect against threats
- Monitoring network and system activity for any suspicious behavior
- Responding to and mitigating security incidents
- Updating security protocols and recommending improvements
- Providing guidance and training to staff members on security best practices
Step 1: Acquiring the Required Skills
To embark on a career as a Cyber Security Analyst, you will need to possess a combination of technical knowledge, analytical skills, and the ability to think critically. The essential skills include:
- Networking: Understanding of network protocols, devices, and architectures
- Operating Systems: Proficiency in various operating systems, such as Windows, Linux, and macOS
- Programming & Scripting: Knowledge of programming languages like Python, Java, C++, and ability to write scripts for automation
- Security Frameworks: Familiarity with security frameworks like NIST, ISO 27001, and CIS
- Web Applications: Understanding of web application vulnerabilities and secure coding practices
- Cryptography: Knowledge of encryption algorithms and techniques
- Malware Analysis: Ability to analyze and identify malicious software
- Problem-Solving: Strong analytical and critical thinking skills to troubleshoot security issues
- Communication: Effective written and verbal communication skills to convey complex security concepts
Step 2: Obtaining the Relevant Education
A formal education in Cyber Security or a related field is crucial to acquire in-depth knowledge and gain hands-on experience. Several educational paths can lead to a career in Cyber Security:
- Bachelor's Degree: Pursue a Bachelor's degree in Cyber Security, Computer Science, Information Technology, or a related field.
- Certifications: Obtain industry-recognized certifications such as CompTIA Security+, Certified Information Systems Security Professional (CISSP),and Certified Ethical Hacker (CEH).
- Master's Degree: Pursue a Master's degree in Cyber Security or a related domain for advanced knowledge and specialization.
- Internships & Practical Experience: Gain practical experience through internships, volunteering, or participating in cybersecurity competitions.
Step 3: Gaining Hands-On Experience
Hands-on experience is crucial to becoming a successful Cyber Security Analyst. Here are some ways to gain practical experience:
- Cybersecurity Projects: Work on personal or open-source projects to enhance your skills and showcase your abilities.
- Internships: Seek internship opportunities with organizations that value cybersecurity to gain practical experience.
- Cybersecurity Clubs & Organizations: Join cybersecurity clubs or organizations where you can collaborate with like-minded individuals.
- Capture The Flag (CTF) Competitions: Participate in CTF competitions to solve cybersecurity challenges and demonstrate your problem-solving abilities.
- Online Resources & Training: Continuously learn and stay updated with the latest cybersecurity trends and tools through online resources and training platforms.
Step 4: Nurturing a Security Mindset
Beyond technical skills and knowledge, developing a security mindset is essential as a Cyber Security Analyst. Some key aspects of a security mindset include:
- Curiosity and Continuous Learning: Stay curious, embrace new technologies, and continuously learn about emerging threats and mitigation techniques.
- Attention to Detail: Pay attention to even the smallest details, as a minute oversight can cause significant security breaches.
- Ethical Conduct: Adhere to professional ethics, abide by legal boundaries, and respect user privacy.
- Adaptability: Be adaptable, as the security landscape is ever-evolving, and staying ahead requires willingness to adapt and learn new techniques.
- Teamwork: Collaborate effectively with other teams, as cybersecurity is a team effort involving various stakeholders.
Step 5: Building a Professional Network
Networking plays a crucial role in the cybersecurity field. Building connections with professionals in the industry can provide valuable insights, mentorship, and opportunities. Here are some ways to build a professional network:
- Join Cybersecurity Communities: Participate in forums, social media groups, and attend cybersecurity events to connect with like-minded professionals.
- LinkedIn: Create a professional LinkedIn profile and engage with cybersecurity experts and recruiters.
- Conferences and Workshops: Attend cybersecurity conferences and workshops to meet industry professionals and expand your network.
- Mentorship: Seek mentorship from experienced professionals who can guide you in your cybersecurity journey.
- Professional Certifications: Certifications often provide access to professional communities and networking opportunities.
Step 6: Landing Your First Job
Once you have acquired the necessary skills, education, experience, and built a professional network, it's time to embark on your career as a Cyber Security Analyst. Here are some tips to help you land your first job:
- Refine Your Resume: Tailor your resume to highlight your skills, projects, internships, and certifications relevant to cybersecurity.
- Job Search: Utilize popular job search websites, professional networks like LinkedIn, and engage with recruitment agencies specializing in cybersecurity roles.
- Interview Preparation: Research common cybersecurity interview questions, practice your answers, and be prepared to showcase your technical skills and problem-solving abilities.
- Continued Learning: Stay updated with the latest cybersecurity trends, technologies, and tools to demonstrate your commitment to professional growth.
- Security Clearances: Certain cybersecurity roles may require obtaining security clearances, so be prepared for additional vetting processes.
Becoming a Cyber Security Analyst is an exciting and rewarding career choice. As businesses and individuals become increasingly reliant on technology, the demand for skilled professionals who can protect against cyber threats continues to rise. By following the steps outlined in this guide, you can pave your way to becoming a successful Cyber Security Analyst and make a real difference in the fight against cybercrime.
4.3 out of 5
| Language | : | English |
| File size | : | 16701 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Word Wise | : | Enabled |
| Print length | : | 281 pages |
| Lending | : | Enabled |
Not sure how to start a career in cybersecurity? You’ve finally came to the right place…
This is the first of a 3-phase course that cater to beginners that are interested in but are timid about breaking into the field of IT. In this course I counter that apprehension with simplified explanations and mentorship-style language. Rather than providing a list of theories and concepts to memorize, you will gain hands on, true-to-life experiences. In addition to this book, you also have the option to watch enacted videos of every lesson in this course at www.pjcourses.com.
Here’s our game plan:
•This book covers Phase 1 – In this phase, I will introduce you to a simulated government agency where you are task with completing their FISMA Compliance (System A&A). You will need to complete RMF Steps 1-5 for the organization.
•Phase 2- We will administer over three popular security tools: SPLUNK, Nessus and Wireshark. After that we will have some fun by learning a few hacking techniques.
•Phase 3 - I will provide you with a game plan to study for your CEH and CISSP exam. Then I will show you where to apply for cybersecurity jobs and how to interview for those jobs
If you’re ready, let’s get started!

 Samuel Ward
Samuel WardTake Control Of Your Network Marketing Career
Are you tired of working...

 Bryson Hayes
Bryson HayesThe Enigmatic Talent of Rype Jen Selk: A Musical Journey...
When it comes to musical prodigies,...

 Norman Butler
Norman ButlerUnveiling the Rich History and Poetry of Shiraz in...
When it comes to the cultural...

 Cade Simmons
Cade SimmonsHow Impatience Can Be Painful In French And English
: In today's fast-paced world, impatience...

 William Shakespeare
William ShakespeareSewing For Sissy Maids - Unleashing Your Creative Side
Are you ready to dive...

 Harry Hayes
Harry HayesGST Compensation to States: Ensuring Fiscal Stability...
In the wake of the COVID-19 pandemic,...

 Rodney Parker
Rodney ParkerLearn How to Play Blackjack: A Comprehensive Guide for...
Blackjack, also known as twenty-one, is one...

 Wade Cox
Wade CoxComplete Guide Through Belgium And Holland Or Kingdoms Of...
Welcome, travel enthusiasts, to a...

 Jack Butler
Jack Butler15 Eye Popping Projects To Create with Felt Decorations
Felt decorations have become a popular craft...

 Dennis Hayes
Dennis HayesFirst Aid For Teenager Soul Mini Book Charming Petites...
The teenage years can...

 Brett Simmons
Brett SimmonsFrom Fear To Freedom - Overcoming Your Fears and Living a...
Are you tired of living in...

 Carl Walker
Carl WalkerSmoking Ears And Screaming Teeth: The Shocking Truth...
Smoking has long been known to cause a host of...
Light bulbAdvertise smarter! Our strategic ad space ensures maximum exposure. Reserve your spot today!

 Samuel BeckettDiscover the Empowering Tales of the Plus Size Diva: Unleashing Confidence...
Samuel BeckettDiscover the Empowering Tales of the Plus Size Diva: Unleashing Confidence...
 Joseph HellerComprehensive Step By Step Guide On Raising Strong Healthy Ducks - Dealing...
Joseph HellerComprehensive Step By Step Guide On Raising Strong Healthy Ducks - Dealing...
 Harvey HughesThe Ultimate Guide to Knitting Lovely Mittens - Create Beautiful and Warm...
Harvey HughesThe Ultimate Guide to Knitting Lovely Mittens - Create Beautiful and Warm... Winston HayesFollow ·10k
Winston HayesFollow ·10k Arthur MasonFollow ·13.6k
Arthur MasonFollow ·13.6k Dominic SimmonsFollow ·18.2k
Dominic SimmonsFollow ·18.2k Brody PowellFollow ·13.9k
Brody PowellFollow ·13.9k Gabriel MistralFollow ·14.1k
Gabriel MistralFollow ·14.1k Samuel Taylor ColeridgeFollow ·15.6k
Samuel Taylor ColeridgeFollow ·15.6k Willie BlairFollow ·4.9k
Willie BlairFollow ·4.9k José SaramagoFollow ·5.5k
José SaramagoFollow ·5.5k
















